Understanding VLAN: The Backbone of Network Segmentation
In today’s interconnected world, efficient and secure network management is critical. Virtual Local Area Networks provide a robust solution for network segmentation, enhancing both performance and security. This blog post delves into the intricacies of VLAN technology, its configuration, and its benefits for modern networks.
What is a VLAN?
A VLAN (Virtual Local Area Network) is a method to logically segment a network. The network can dynamically change and is not dependent on the physical network topology. This technology is defined by the IEEE 802.1Q standard, also known as dot1q.
In essence, a VLAN allows a group of computers to communicate as if they were on the same physical network, regardless of their actual physical locations. This logical grouping enhances network management, security, and performance.
The Need for VLANs
Without VLANs, a single switch represents a single broadcast domain. In a large network with many users, this can lead to broadcast storms that degrade network performance. It is not good to have numerous users in the same broadcast domain. That increases the risk of network attacks and data breaches. VLANs address these issues by isolating groups of users, thus improving security and reducing broadcast traffic.
Virtual Local Area Network Configuration: The Basics
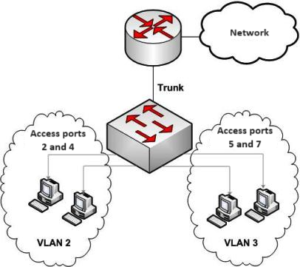
We configure VLANs on switches, with each port on the switch assigned to a specific VLAN by the network administrator. There are two main types of VLAN connections:
- Trunk Links
- Access Links
Trunk Links
A trunk link is a tagged connection used to connect switches to each other or to routers. It carries traffic for multiple VLANs, with each frame tagged to indicate its VLAN membership. This allows devices on the same VLAN but connected to different switches to communicate as if they were on the same local network.
Access Links
An access link is an untagged connection used to connect end devices like computers to the switch. Traffic on access links does not have VLAN tags. When traffic from an access link goes through a trunk link, a VLAN tag is added to indicate its VLAN membership.
Inter-VLAN Communication
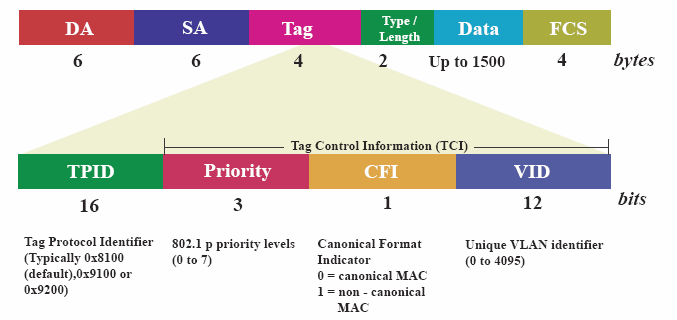
Devices on different VLANs cannot communicate directly; they need a Layer 3 (L3) device, such as a router or an L3 switch, to route traffic between them. This involves the use of 802.1Q headers, which contain VLAN tagging information. The 802.1Q header ensures that traffic is appropriately segmented and routed to the correct VLAN.
L3 Switching and VLANs
Layer 3 switches function similarly to routers, with routing tables that manage traffic between different VLANs. L3 switching works in two ways:
- Hardware-Based (ASIC)
- Software-Based
Hardware-Based L3 Switching
This uses Application-Specific Integrated Circuit (ASIC) chips to handle the switching, providing high-speed data processing and efficient network performance.
Software-Based L3 Switching
This relies on the device’s CPU and software to manage the switching process. While generally slower than hardware-based solutions, it offers greater flexibility and is suitable for smaller networks.
Router Configuration for VLANs
When using a router to manage VLANs traffic, its interface is divided into multiple sub-interfaces, each corresponding to a different VLAN. Each sub-interface has an IP address within the VLAN’s range, serving as the default gateway for that VLAN. Additionally, the sub-interface must be configured with the appropriate VLAN and trunking protocol.
Conclusion
VLANs are a vital component of modern network design, offering a powerful way to segment networks logically. By improving network performance and security, VLANs enable efficient and scalable network management. Understanding VLAN configuration and the role of trunk and access links, as well as L3 switching, is essential for any network engineer aiming to optimize their network infrastructure.
Implementing VLANs correctly can significantly enhance the efficiency and security of your network, making it adaptable to the dynamic needs of today’s digital environment.